Introduction to NIST CSF 2.0
The National Institute of Standards and Technology (NIST) is a U.S. federal agency that develops technology, measurement, and standards to enhance productivity and facilitate trade. In 2014, NIST released the first version of the Cybersecurity Framework (CSF 1.1) to provide guidelines and best practices for organizations to manage better and reduce cybersecurity risks.
CSF 1.1 outlined industry standards, guidelines, and practices across six core functions - Govern, Identify, Protect, Detect, Respond, and Recover. It enabled organizations to assess and improve their ability to prevent, detect, and respond to cyber-attacks. CSF 1.1 was widely adopted, expanding usage across critical infrastructure and other sectors.
In February 2024, NIST released an updated version, the Cybersecurity Framework 2.0 (CSF 2.0), to reflect the evolving cybersecurity landscape. CSF 2.0 provides a comprehensive approach for organizations to understand, manage, and reduce cybersecurity risk. It introduces new features, such as customizable profiles, to tailor the framework implementation to an organization's risk disposition and resources. Other key additions include a greater emphasis on supply chain risks, improved usability, and additional references like the NIST Privacy Framework. NIST CSF 2.0 represents an evolution that builds on the impact and success of the original framework.
What is NIST CSF 2.0?
The NIST Cybersecurity Framework (CSF) is a voluntary framework developed by the National Institute of Standards and Technology (NIST) that provides organizations with guidelines and best practices for managing cybersecurity risks. The latest version, CSF 2.0, was released in 2024 as an update to CSF 1.1, published in 2018.
NIST CSF 2.0 provides a comprehensive approach to cybersecurity by identifying core cybersecurity activities, assessing current practices, and guiding improvements. At its core, NIST CSF 2.0 consists of three main components:
| Component | Description |
|---|---|
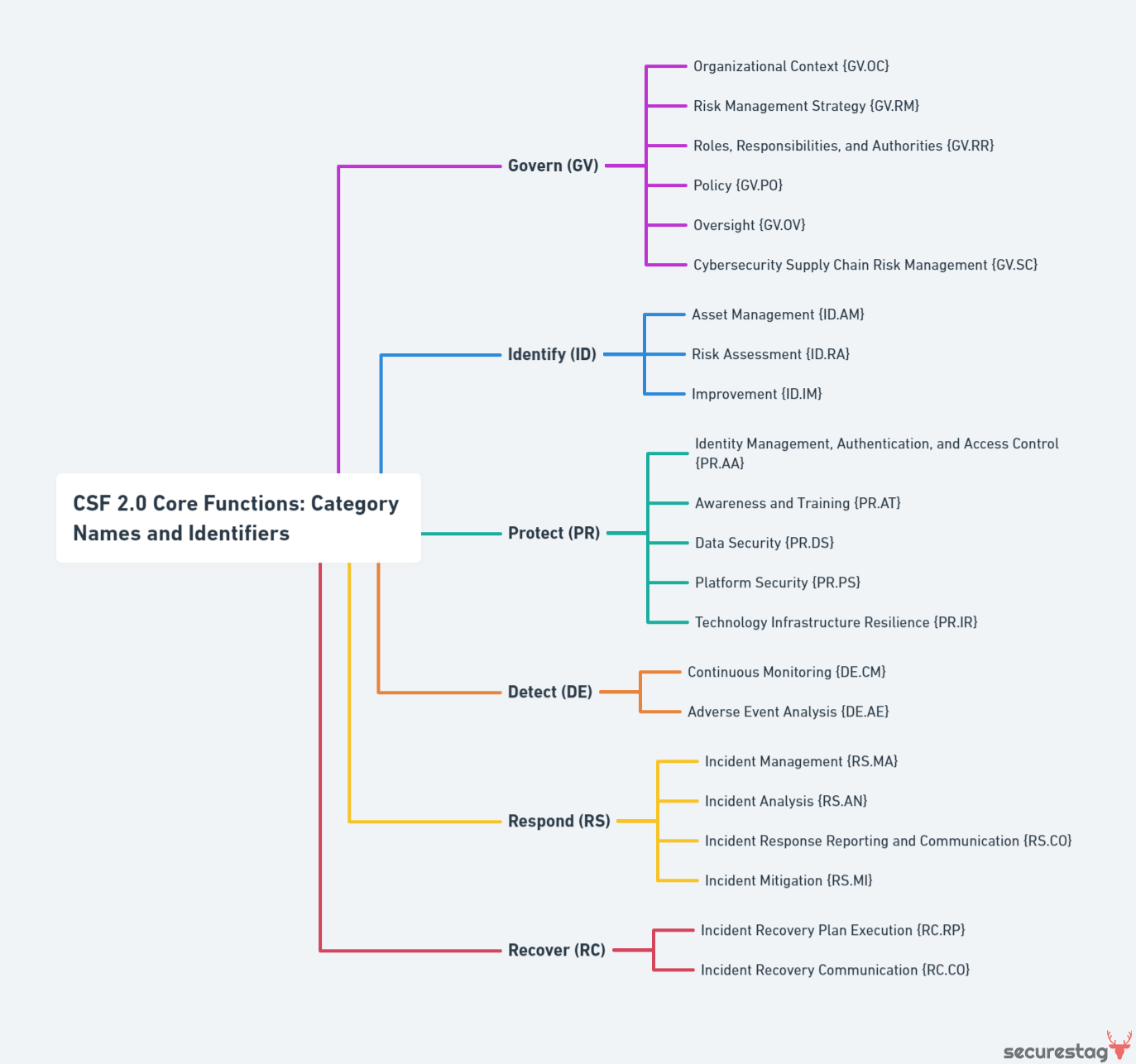
| The Framework Core | A set of cybersecurity activities and outcomes grouped into six Functions: Govern, Identify, Protect, Detect, Respond, and Recover. These serve as the heart of the framework. |
| The Framework Profile | Allows organizations to customize the Framework to their specific needs by selecting priorities for the components. |
| The Framework Implementation Tiers | Provide context for the organization's cybersecurity approach and progress made. |
NIST CSF 2.0 aligns with globally recognized best practices and industry standards for cybersecurity. It serves as a living document that will continue evolving as technology advances and new cyber threats emerge. With its flexible and customizable nature, CSF 2.0 can be applied by organizations of any size or industry to manage cyber risks and improve their cybersecurity posture.
Evolution from CSF 1.1 to 2.0: What's New?
The NIST Cybersecurity Framework (CSF) was originally published in 2014 as version 1.1. After years of use and feedback from stakeholders, NIST determined it was time to update the framework to version 2.0 to better meet the needs of modern organizations. NIST CSF 2.0 contains several notable changes and new capabilities:
- Expanded guidance on governance. While CSF 1.1 contained some governance guidance, version 2.0 goes into further depth on processes for establishing, communicating, and reviewing cybersecurity objectives within an organization.
- Increased focus on vulnerability management. In 2.0, the vulnerability management function in the Core has been expanded to cover the identification, analysis, and mitigation of vulnerabilities. This reflects the increasing recognition of how vulnerabilities lead to exploits and breaches.
- New appendix covering control baselines. Version 2.0 introduces an entirely new appendix providing control baseline examples mapped to CSF functions. This helps organizations implement specific controls for various best practice standards and regulations.
- Emphasis on diversity, equity & inclusion. The updated framework aims to promote more inclusive cybersecurity practices, including guidance on reducing bias in processes and controls.
- Focus on supply chain cybersecurity. New sections address cybersecurity practices associated with suppliers, service providers, and partner interactions. This reflects rising supply chain threats.
NIST determined it was crucial to update the framework to address the changing cyber risk landscape and provide more comprehensive guidance. CSF 2.0 represents the state-of-the-art approach for managing cybersecurity risk in modern environments.
Understanding the CSF Core: The Heart of the Framework
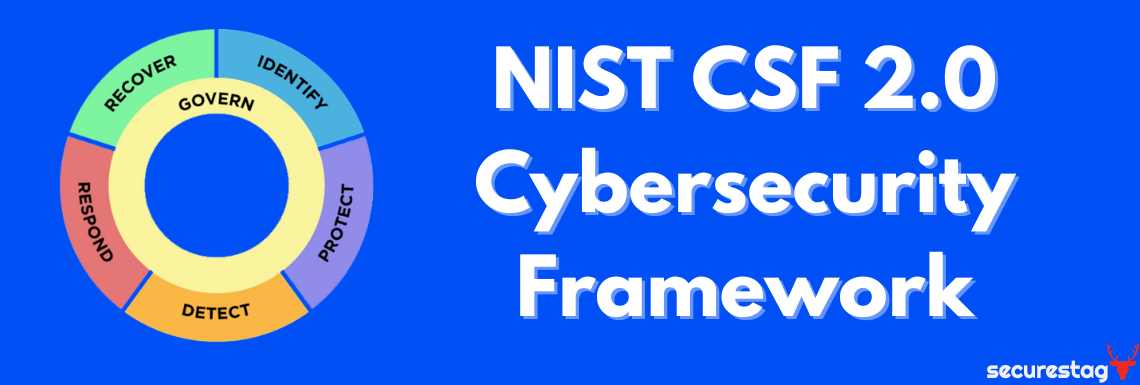
The Core is the heart of the NIST CSF and contains cybersecurity activities and desired outcomes that are common across sectors and organizations. It consists of six high-level Functions: Govern, Identify, Protect, Detect, Respond, and Recover. Within each Function are Categories and Subcategories that provide specific cybersecurity outcomes.
The Six Functions
The six Functions represent a high-level, strategic view of the lifecycle of an organization's management of cybersecurity risk. They provide a concise representation of the outcomes an organization should achieve through cybersecurity risk management:
- Govern - Develop and communicate the organization's cybersecurity risk management policies and strategy. The Govern function is newly added in NIST CSF 2.0, and is crucial for establishing an organization's approach to managing cybersecurity risk. It involves defining roles, responsibilities, and the process for integrating cybersecurity into the overall enterprise risk management. This strategic approach helps ensure that efforts across the Identify, Protect, Detect, Respond, and Recover functions are aligned with the organization's goals, compliance requirements, and stakeholder expectations. Key activities within this function focus on developing a comprehensive cybersecurity strategy, establishing governance structures to support cybersecurity efforts, and monitoring the effectiveness of cybersecurity policies and practices.
- Identify - Develop an organizational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities. The activities in the Identify Function are foundational for effective use of the Framework. Understanding the business context, the resources that support critical functions, and the related cybersecurity risks enables an organization to focus and prioritize its efforts. Categories within this Function include Asset Management, Business Environment, Governance, Risk Assessment, and Risk Management Strategy.
- Protect - Develop and implement appropriate safeguards to ensure the delivery of critical services. The Protect Function supports the ability to limit or contain the impact of a potential cybersecurity event. Categories within this Function include Identity Management and Access Control, Awareness and Training, Data Security, Information Protection Processes and Procedures, Maintenance, and Protective Technology.
- Detect - Develop and implement appropriate activities to identify the occurrence of a cybersecurity event. The Detect Function enables the timely discovery of cybersecurity events. Categories within this Function include Anomalies and Events, Security Continuous Monitoring, and Detection Processes.
- Respond - Develop and implement appropriate activities to take action regarding a detected cybersecurity incident. The Respond Function supports the ability to contain the impact of a potential cybersecurity incident. Categories within this Function include Response Planning, Communications, Analysis, Mitigation, and Improvements.
- Recover - Develop and implement appropriate activities to maintain resilience plans and restore any capabilities or services that were impaired due to a cybersecurity incident. The Recover Function supports timely recovery to normal operations to reduce the impact of a cybersecurity incident. Categories within this Function include Recovery Planning, Improvements, and Communications.
Together, these six Functions provide a high-level, strategic view of cybersecurity risk management's lifecycle. They guide organizations in managing threats and protecting critical assets through prevention, detection, and timely response.
Structuring the Framework: Profiles and Tiers
Organizational Profiles: Customizing Your Cybersecurity Strategy
Organizational profiles are a vital component of the NIST CSF 2.0 for tailoring the framework to your organization's specific needs. Profiles allow organizations to customize the framework by prioritizing and selecting controls from the core that are most relevant to their risk management priorities, threats, and vulnerabilities.
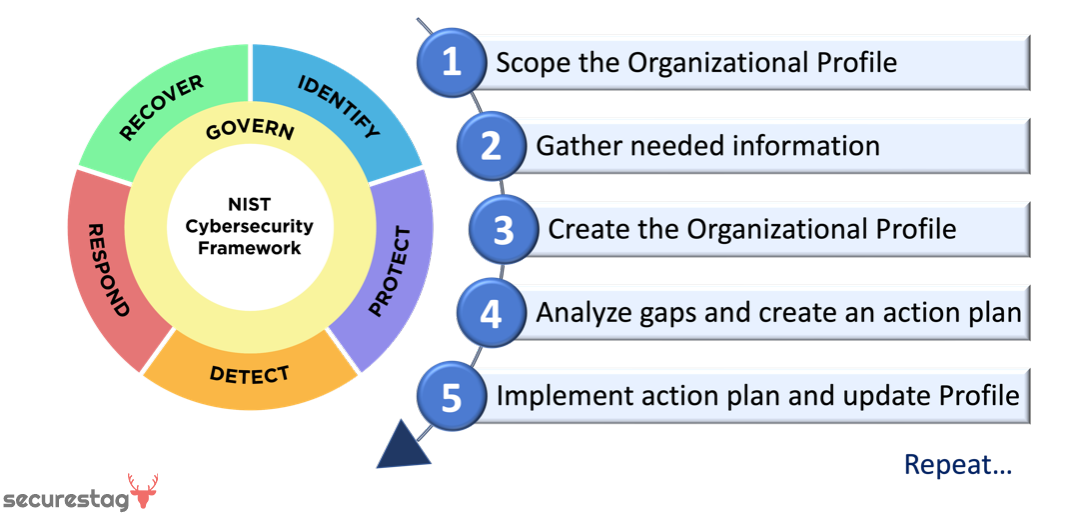
Organizations can develop target profiles to strategically focus their cybersecurity efforts on a subset of activities representing their priorities. Current and desired target profiles can be compared to support cybersecurity risk management decisions and measure improvement over time. Organizational profiles are flexible and adaptable as circumstances change.
Tiers: Calculating Your Cybersecurity Maturity
The tiers component of NIST CSF 2.0 provides context on how an organization views cybersecurity risk and how cybersecurity practices are integrated into broader risk management. The tiers describe the degree of rigor, formality, and integration of cybersecurity into broader risk management based on business needs.
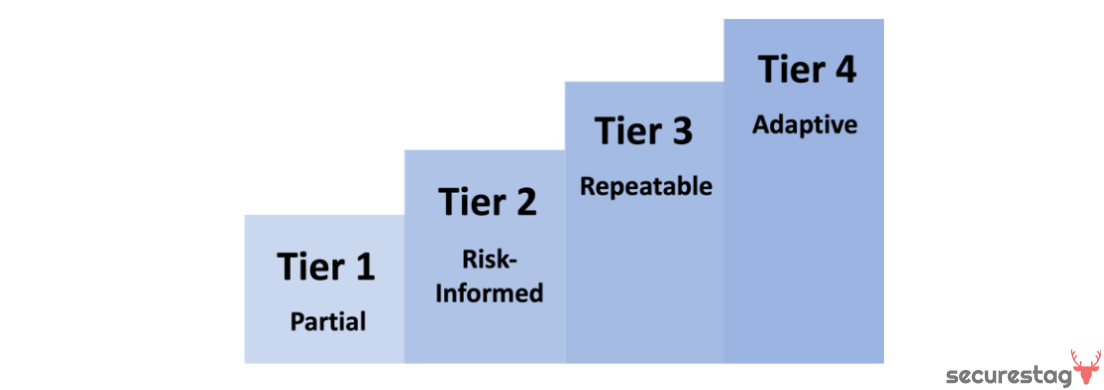
There are four tiers, ranging from Partial (Tier 1) to Adaptive (Tier 4). A higher tier indicates greater cybersecurity maturity and understanding of cybersecurity risk. However, a higher tier is not necessarily better. Organizations should determine the tier that appropriately supports their risk management needs. Tiers help assess progress in managing cybersecurity risk over time.
Implementing NIST CSF 2.0
The most important step in leveraging NIST CSF 2.0 is developing a robust implementation plan and strategy. Organizations should start by reviewing their current cybersecurity policies, controls, and maturity level to identify gaps that CSF 2.0 can help fill. Teams can use the Framework Core's Functions, Categories, and Subcategories as a reference when mapping their existing cybersecurity initiatives and determining where improvements are needed.
Organizations should consider all relevant stakeholders and business processes when developing an implementation roadmap. Cross-functional collaboration is key - IT teams will need to work closely with legal, risk management, executive leadership, and others. The implementation plan should have defined milestones, success metrics, resource needs, and timelines.
Putting the plan into action requires buy-in at all levels of the organization. Training programs, especially for non-technical employees, build workforce cyber readiness. Once the framework is implemented, conducting audits or maturity assessments helps verify that cybersecurity controls are operating as intended. Ongoing maintenance and updates to the program are also critical as threats evolve.
Supplemental resources that provide guidance on implementing the CSF include NIST's online CSF Implementation Guidance, the CSF Starter Implementation Guide, and for federal agencies - the Federal CSF Implementation Quick Start Guide. Utilizing these references helps ensure a smooth and effective Framework deployment.
The Impact and Importance of NIST CSF 2.0
The NIST Cybersecurity Framework (CSF) provides organizations with guidance on managing cybersecurity risk in the face of constantly evolving threats. The release of CSF 2.0 in 2022 builds upon the successes of the original framework while incorporating lessons learned. Organizations implementing CSF 2.0 can expect several benefits that enhance their cybersecurity posture.
One key advantage of NIST CSF 2.0 is that it enables organizations to take a strategic, risk-based approach to cybersecurity. By leveraging the framework's core components, like the Functions, Profiles, and Tiers, businesses can develop a plan tailored to their specific assets, risks, and risk appetite. This allows them to prioritize cybersecurity spending and direct resources to the areas of most significant concern. CSF also promotes evaluating tradeoffs between security and other organizational goals.
Additionally, the broad acceptance and use of CSF means that implementing version 2.0 enables better communication and coordination within industries and supply chains. Organizations can use the framework's common language to report and benchmark cybersecurity risk information with partners, regulators, and insurers. This also simplifies vendor evaluations and audits.
At its core, CSF 2.0 helps businesses improve their cybersecurity capabilities over time. The framework guides organizations through assessing the current state, defining an ideal future state via Profiles, and then taking manageable steps to reduce gaps via Tiers. This incremental approach means CSF adoption can lead to meaningful risk reduction and enhanced resilience against threats.
Looking Ahead: The Future of Cybersecurity with NIST CSF 2.0
The NIST Cybersecurity Framework will continue to evolve and adapt as technology and threats change. Even with the release of version 2.0, NIST recognizes the framework is not a static document and plans for ongoing updates and revisions. As stated on their website, "Updating the NIST Cybersecurity Framework – Journey To CSF 2.0", continuous improvement is a key objective to "keep pace with technology and threat trends, integrate lessons learned, and move best practice to common practice."
Some future outlooks for the framework include integrating new technologies like Internet of Things (IoT) devices and cloud computing. As our digital landscape shifts, so will cyber risks and the recommended safeguards. Other focus areas are operational technology (OT) and industrial control systems (ICS), which present distinct challenges compared to traditional IT systems. Tailoring guidance for these sectors will be imperative. Lastly, artificial intelligence (AI) and machine learning (ML) will likely play a more significant role in cyber defense. Incorporating these emerging tools into the framework will strengthen protection for organizations.
While the future direction continues to take shape, the CSF promises to remain an adaptable, risk-based model that establishes best practices for cybersecurity. The framework's voluntary and flexible nature allows it to continuously integrate new knowledge and technologies. As threats persist and transform, NIST and stakeholders will keep the CSF current and impactful.
Conclusion: Adopting NIST CSF 2.0 for Enhanced Cybersecurity
The release of the NIST Cybersecurity Framework (CSF) Version 2.0 provides organizations with a significant update to build cyber resilience. CSF 2.0 expands the scope of the framework to include privacy risks and supply chain concerns, reflecting the evolving cyber landscape and interconnected nature of cybersecurity, privacy, and supply chain risks. With its flexible structure and focus on continuous improvement, CSF 2.0 enables organizations to tailor cybersecurity strategies to their specific needs and maturity levels.
At its core, CSF 2.0 provides a comprehensive approach to managing cybersecurity through its six functions: Govern, Identify, Protect, Detect, Respond, and Recover. Organizations can develop customized profiles to reduce risks and demonstrate cybersecurity maturity by implementing these functions. CSF 2.0 also emphasizes using tiers to evaluate the current state and drive progress in managing risks.
Overall, CSF 2.0 delivers a critical update to help organizations address evolving threats and strengthen cybersecurity. By embracing CSF 2.0's expanded scope, updated core, and focus on tailored implementation, organizations can build cyber resilience today and into the future. CSF 2.0 provides a strategic roadmap to manage cyber risks and demonstrates the importance of cybersecurity as an ongoing journey of improvement.
