
Table of Contents
Understanding Identity and Access Management (IAM)
Identity and Access Management (IAM) is a framework of policies and technologies for ensuring the right users have appropriate access to an organization’s technology resources. IAM establishes digital identities for users and devices to control access to applications, systems, and data.
IAM manages user identities and access privileges through features like authentication, authorization, roles, policies, and auditing. It provides a centralized way to manage users and control who has access to which resources.
The key components of an IAM system include:
- Identity providers – validate and manage user identities.
- Access management – authorizes which users can access resources.
- Federation services – enables SSO across domains.
- Directory services – store identity data like users and roles.
- Identity lifecycle management – manages user onboarding and offboarding.
The main benefits of implementing IAM include:
- Enhanced security – restricts access and prevents unauthorized use.
- Improved compliance – grants least privilege access for regulatory requirements.
- Greater efficiency – automates account provisioning and de-provisioning.
- Better visibility – provides audit trails of user activities.
IAM is critical for regulatory compliance as it provides the access controls and audit capabilities needed to adhere to policies like PCI DSS, HIPAA, and GDPR.
Key features of IAM platforms include single sign-on (SSO), multi-factor authentication (MFA), role-based access control (RBAC), user provisioning/de-provisioning, and identity analytics.
Implementing Identity and Access Management (IAM)
Steps to implement IAM
The first step in implementing an IAM system is to define the business requirements and identity management goals. This involves identifying the resources that need access, the users who require access, and the appropriate access levels.
Once requirements are defined, an IAM framework that aligns with the organization’s needs can be designed. The framework outlines the identity and access controls, integrations with existing systems, and processes for managing identities and access.
Key steps for implementation include:
- Integrating IAM with user directories like Active Directory.
- Developing policies and role definitions.
- Configuring user provisioning and de-provisioning.
- Implementing single sign-on (SSO).
- Rolling out multi-factor authentication (MFA).
- Training administrators and end users.
Identity and Access Management on AWS
AWS provides robust IAM capabilities through AWS IAM to manage access to AWS resources. The high-level steps to implement IAM on AWS include:
- Creating IAM users and groups.
- Defining IAM roles and creating policies.
- Enabling MFA.
- Setting up federated access with identity providers.
- Using access levels and credentials.
- Enabling integration with AWS services.
- Monitoring IAM through logs and audits.
Key components such as the Identity Center, permissions policies, and Access Analyzer help secure and manage access.
Challenges of Identity and Access Management (IAM) implementation
Some key challenges in implementing an IAM system include:
- Integrating legacy systems with IAM.
- Overcoming resistance to change in processes.
- Achieving alignment across business and IT teams.
- Preventing role proliferation and access creep.
- Providing seamless SSO experiences.
- Ensuring the accuracy of user data.
- Building flexibility to accommodate future growth.
Role of Identity and Access Management (IAM) in identity management
IAM plays a central role in managing digital identities and access by:
- Centralizing identity data and access policies.
- Automating identity administration.
- Enforcing access controls consistently.
- Providing single sign-on across applications.
- Enabling self-service identity management.
- Supporting strong authentication mechanisms.
This enhances security and compliance while improving efficiency and user experience.
Managing access for on-premises Identity and Access Management (IAM)
To manage access for on-premises IAM environments, strategies include:
- Using identity providers like Active Directory.
- Implementing Identity Bridge to AWS.
- Enabling integration through LDAP and SAML.
- Providing secure VPN for on-premises access.
- Deploying hybrid models with AD-integrated SSO.
- Managing sessions and tokens.
- Logging activity for on-prem systems.
This allows organizations to extend IAM capabilities for their hybrid infrastructure securely.
Access Management and Security
Role-based access control (RBAC) is a key access management component in IAM. RBAC restricts access to resources and systems based on defined roles and permissions. This improves security by preventing unauthorized access while streamlining access rights automation.
Some key benefits of RBAC include:
- Improved security by restricting access based on roles.
- Operational efficiency by reducing manual tasks and paperwork.
- Flexibility to add or change roles as needed.
Identity providers are another essential element of access management in IAM. They allow single sign-on authentication and secure access to resources. Standard identity providers used with IAM are Microsoft Active Directory, LDAP, SAML, and social login providers.
Managing user identities and secure access is a core function of IAM. This involves provisioning user accounts, setting access levels, and implementing controls like multi-factor authentication. Privileged access management provides additional controls for high-level admin accounts.
Access privileges define the level of access users have within the IAM system. This ranges from basic access to full administrative rights. Appropriate access privileges help enforce the principle of least privilege.
IAM Technologies and Solutions
Overview of IAM tools and technologies
Identity and access management (IAM) solutions encompass a wide range of tools and technologies for managing digital identities and controlling access to resources. These include identity providers, authentication systems, authorization management, access governance, and more.
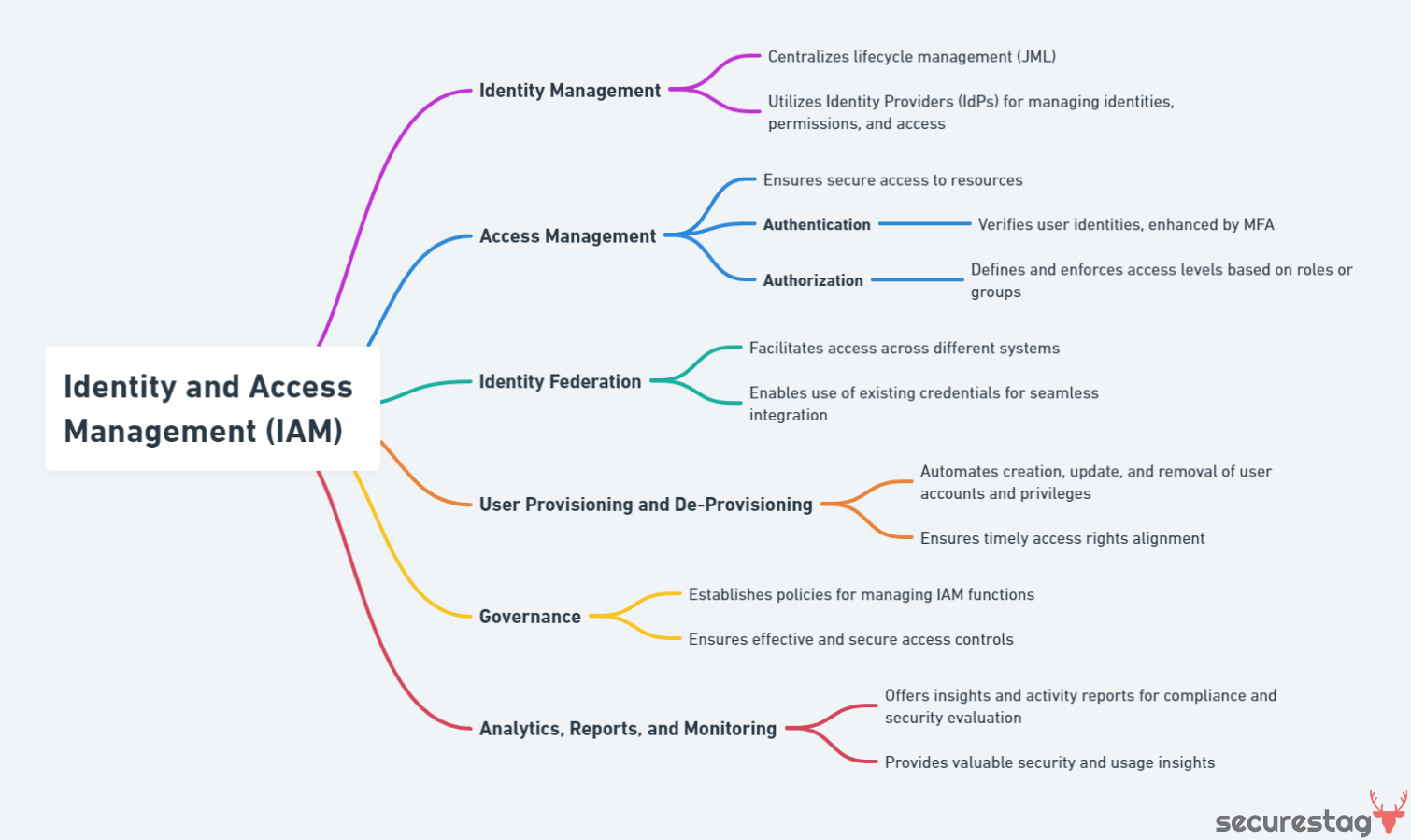
Some key categories or core functionalities of IAM technologies include:
- Identity Management: Centralizes the lifecycle management (Joiner-Mover-Leaver-JML) of digital identities, utilizing Identity Providers (IdPs) to manage user identities, permissions, and access levels efficiently.
- Access Management: Ensures secure and appropriate access to resources, combining authentication and authorization mechanisms:
- Authentication verifies user identities, enhanced by MFA, for additional security.
- Authorization precisely defines and enforces access levels based on user roles or groups.
- Identity Federation: Facilitates access across different systems, enabling users to utilize existing credentials for seamless system integration.
- User Provisioning and De-Provisioning: Automates the creation, update, and removal of user accounts and their privileges, ensuring timely access rights alignment.
- Governance: Establishes policies and procedures for managing, monitoring, and auditing IAM functions to ensure effective and secure access controls.
- Analytics, Reports, and Monitoring: Offers insights and generates activity reports (e.g., login times, accessed systems) for compliance adherence and security evaluation, offering valuable security and usage insights.
Best practices for using Identity and Access Management (IAM)
Effective use of IAM relies on the following security best practices:
- Adopt least privilege access – Grant users only the permissions necessary to perform their role.
- Implement separation of duties – Divide privileged tasks across users.
- Frequently review access – Routinely evaluate and adjust user access rights.
- Enforce strong authentication – Require complex passwords, biometrics, or MFA.
- Monitor user activities – Log and analyze user behavior to catch anomalies.
- Educate users on security – Establish policies and train staff on secure practices.
Implementing the IAM framework
A robust IAM framework includes identity provisioning, authentication, authorization, access management, and auditing capabilities. Key steps involve:
- Defining access policies aligned to business needs.
- Selecting suitable IAM solutions for your environment.
- Configuring role-based access controls and privileges.
- Integrating IAM tools with existing infrastructure.
- Rolling out SSO, MFA, and stringent access controls.
- Continuously managing and refining access policies and controls.
IAM as a product or platform
Organizations can implement IAM functionality through individual point solutions for capabilities like SSO or MFA. A more robust approach is adopting an integrated IAM platform from well-known vendors like Okta, Ping Identity, One Identity, ForgeRock, IBM Security, or Microsoft.
Key benefits of an IAM platform include centralization, consolidation, and consistency of access policies across applications and environments.
Security assertion markup language (SAML) in IAM
SAML is an XML-based open standard for exchanging authentication and authorization data between parties, commonly used for SSO.
SAML enables identity providers to pass user authentication credentials to service providers for fast and secure access across systems. This eliminates re-authenticating when switching between applications.
Future of Identity and Access Management (IAM)
Latest advancements and trends in IAM
In recent years, identity and access management (IAM) has seen rapid innovation and development. Some of the latest trends shaping the future of IAM include:
- Passwordless authentication – Using biometrics, security keys, and other methods instead of passwords for login and authentication. This improves security and user experience.
- Multicloud access policy standardization – Creating standardized access policies across different cloud providers to simplify management.
- Increased adoption of IAM as a service – More organizations are adopting IAM solutions delivered as cloud services rather than on-premises software, which provides flexibility and scalability.
Enhancements in AWS IAM services and resources
AWS has invested heavily in IAM capabilities for its cloud platform. Recent enhancements include:
- Integration with AWS Single Sign-On (SSO) – Allows centralized access management to multiple AWS accounts and business applications.
- AWS IAM Access Analyzer – Automatically validates that IAM policies grant the least privilege access.
- AWS Lake Formation access control – Granular access control for data stored in AWS Lake Formation.
User identity verification in the future of IAM
Strong identity proofing and authentication will be critical for IAM systems in the future. Emerging technologies like biometrics, decentralized identifiers (DIDs), and self-sovereign identity can provide robust identity verification. This will reduce identity fraud and enhance trust in digital identities.
Challenges and opportunities in implementing IAM in 2024
As organizations expand their Identity and Access Management (IAM) systems, they face several challenges, such as increased complexity, lack of standards, and talent shortages. However, there are opportunities to overcome these challenges by leveraging cloud-based delivery models, Artificial Intelligence (AI) driven analytics, Zero Trust security model, and policy automation. To successfully implement IAM in 2024, organizations need to have a strategic roadmap and adaptable platforms.
Impact of IAM on Digital Identity Landscape
Identity and Access Management (IAM) will continue to play a crucial role in shaping the future of digital identities. With a projected market growth reaching $17.31 billion by 2023 and a compound annual growth rate of 14.10%, IAM technologies are at the forefront of securing digital ecosystems against increasing threats and enabling seamless access management across various platforms.
A significant trend is the adoption of digital identity wallets, with 66% of Americans expecting to have one by 2023. These wallets, aimed at reducing KYC/AML costs, are quickly becoming integral to consumer expectations, indicating a shift towards more user-centric identity verification methods. Moreover, the Liminal Summit 2023 highlights the emergence of identity wallets as a promising solution for managing digital identities in a decentralized and user-centric manner, showcasing the industry’s commitment to innovation and exploration in the field of digital identity.
The impact of IAM on the digital identity landscape is multifaceted, enhancing privacy, interoperability, and user-centricity. As organizations increasingly adopt modern IAM solutions, they are able to strengthen their security and pave the way for a future where digital identity and service access are more seamless and secure.



Comments 1